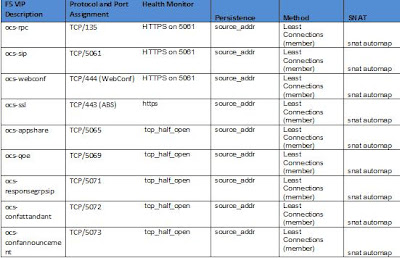
To configure a health monitor for 5061 using the web F5 admin interface (information taken from F5 OCS R1 configuration document):
1. On the Main tab, expand Local Traffic, and then click Monitors. The Monitors screen opens.
2. Click the Create button. The New Monitor screen opens.
3. In the Name box, type a name for the Monitor.
4. From the Type list, select HTTPS.The TCP Monitor configuration options appear.
5. From the Configuration list, select Advanced. The advanced configuration options appear.
6. In the Configuration section, in the Interval and Timeout boxes, type an Interval and Timeout.
7. In the Alias Service Port box, type 5061.
8. Click the Finished button.
From the .conf file it will look something like this:
}
monitor ocs-frontend-sip-5061 {
defaults from https
interval 30
timeout 91
dest *:5061
}
Also, you will need to create a TCP profile with an Idle timeout of1200 seconds and enable TCP resets on idle timeout which will need to be applied to each of the F5 pools created.
Of course all this information is on the internet in various places. The following document is available from MSFT on load balancing requirements for OCS R2 but it’s a general document not specific for F5.
Hopefully this will help someone out there somewhere :-)



